Cybersecurity
Applying Total Quality Management Principles to Cyber Security and IT Management

IT executives and leaders are charged with building scalable, reliable, and secure environments. As more sensitive, regulated, and business-vital documents and transactions are digitized, even traditional businesses must embrace cybersecurity as a way of life. With this comes a mandate to develop and deploy a security program, which necessarily must include a component for continuous improvement. Security threats are constantly evolving, and threat or security fatigue can increase the pressure on security teams to keep up. Adding structure to the continuous improvement process can help relieve some of that pressure to “stay on top of everything” all the time.
Total Quality Management (TQM) and Why It Matters
While it is unclear who first coined the term “Total Quality Management”, the modern incarnation in the US was created by the US Navy. While overall consensus of what is or is not “TQM” is hard to achieve, overall “Total Quality Management” consists of the following key concepts:
- Quality is defined by the customer – In this case, the executives of the company and IT leadership
- Top management is directly responsible for quality improvement
- Quality improvements come from rigorous analysis of the work processes themselves
- Quality is a continuous effort, and isn’t just the responsibility of any one team or group, but the company as a whole
If you look at the TQM philosophy, it’s likely to conclude that it is widely applicable and you’re right. TQM is used widely across the massive organizations where quality and supply chain logistics extend across functional boundaries as well as geographical boundaries. From a cybersecurity perspective, it’s easy for managers and subject matter experts to fall in love with “the next cool tool” or software, but as IT leaders we must take a step back and analyze how to make processes repeatable, and that includes quality assurance for security systems.
Risk Registers the Mitigation Process
The Center for Internet Security defines the ‘classic risk equation’ where risk is a function of vulnerability, threats, and consequence, over countermeasures or technical safeguards.
![]()
As we discussed in the previous section, it’s critical to start with a frank conversation on these topics with every functional team leader or business stakeholder. Sometimes these can even be suppliers, vendors, or even customers that have integrations for just-in-time shipping or other logistics integrations. This allows us to form a good understanding of the systems involved as well as the overall business tolerance for risk (including regulatory requirements). Building a well-documented and socialized ‘Risk Register’ – even if it’s as simple as an excel table – can help the business understand where the blind spots are and what technical safeguards the security architecture team needs to implement. Lastly, this can help create budget-to-risk alignment.

As technical safeguards are implemented, often there is a sense of “relief” that a risk has been mitigated, but this is where the continuous improvement process starts
The “OODA” Loop and Continuous Improvement
The OODA loop is a decision cycle of “observe, orient, decide, and act”, developed by military strategist and United States Air Force Colonel John Boyd for use by fighter pilots and others during combat operations. This decision cycle helps provide structure to continuous improvement and quality assurance meetings/discussions as a way to quickly and efficiently make decisions and create consistency on security platforms that have already been implemented. See the diagram below for a sample of how an OODA loop could create continuous improvement in the vulnerability patching process.
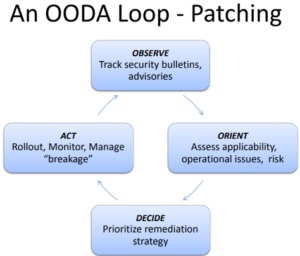
Total Quality Management and the Loop
The quality assurance effort is a continuous loop and isn’t just the responsibility of any one team or group, but the company as a whole. With that in mind, it is important to define Key Performance Indicators (KPIs) and possibly a security dashboard PowerPoint that is refreshed and reviewed weekly to ensure the team is ‘Observing’ and ‘Orienting’ to the right risk and issues, and data-driven decisions can be made by the appropriate teams.
External Validation, Consulting, and Implementation of TQM Principles
We on the consulting practice at Thrive help our customers with implementing industry leading security services but are also frequently asked to help organizations review their security program and the security health of their organization. This frequently starts with a full review not only of the processes and tools in use, but also the program as a whole. It can be beneficial to have a second set of eyes and external validation for an external party to review security practices.
